How to Find the Right SaaS Discovery Method for Your Organization

Before you can find the right SaaS discovery method for your organization, it’s important to learn why finding out your organization’s true SaaS application usage is important. Here are three of the most common reasons why you need an accurate understanding of usage.
1. Reducing risk. Unless you’ve locked down access to the internet, your employees are very likely not going through your formal procurement or SSO to use SaaS applications. Applications not vetted by IT security might not be secure and your employees may not be using strong passwords.
2. Removing complexity. The complexity caused by redundant applications and multiple contracts with the same vendor is a challenge, especially for organizations with distributed IT and procurement and frequent M&A. This “SaaS sprawl” is the biggest challenge in managing SaaS applications.
3. Optimizing cost. Around 30% of SaaS cost is wasted due to unallocated or unused licenses. With SaaS, vendors bundle functionality in tiers. You may be paying for a more expensive tier than you need.
Comparing SaaS discovery methods
Now that you’ve considered your goals for managing your SaaS environment, your next move is to learn how to collect this information so your organization can actually reduce costs, remove complexity and identify risk. There are multiple methods of capturing SaaS details and some may be more appealing than others, depending on your goals and technologies in use. Your specific goals for SaaS app discovery will impact your discovery methods.
Check out the tables below to learn more about each of the methods and their benefits and identify which method is right for you.
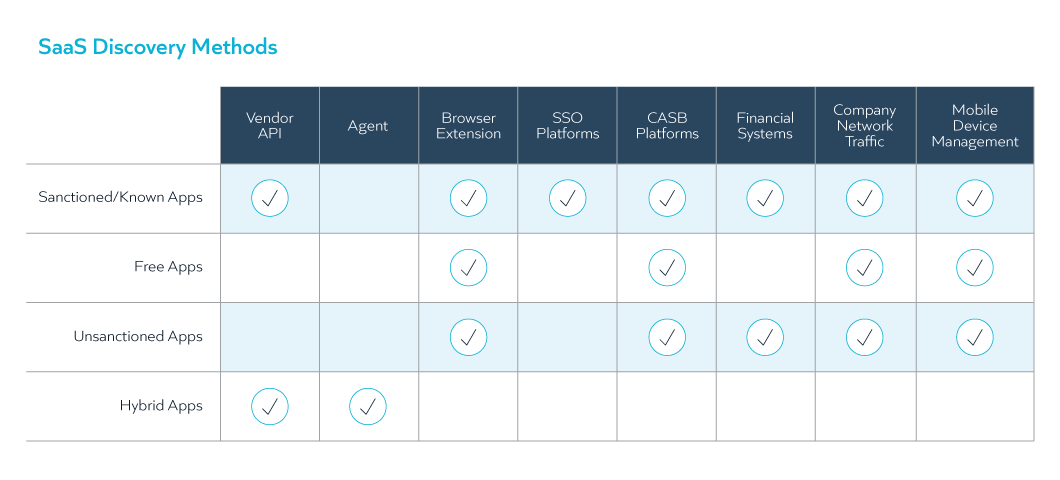
| Discovery Method | Description and Benefits |
| Vendor API | This discovery method is a great option for SaaS applications in which you need to stay on top of license allocations and usage. This method sometimes offers the ability to see usage of specific features and products, so you’ll have the data to downgrade from expensive license tiers if employees are not using the functionality. The downside of using vendor APIs is that you are dependent on the vendor publishing usage data and obtaining it in a readable format to consume if you’re not leveraging a SaaS management tool. |
| Agent | Agents are traditionally used to capture installed software. Some SaaS vendors price application tiers aligned from where the application is used. For example, Microsoft 365 E1 licenses are priced for accessing applications online, but the more expensive E3 license allows users to access applications online and install them on their desktop/PC. The value in detecting from where applications are accessed is the ability to potentially downgrade employees from a more expensive license tier. |
| Browser Extension | The main benefit of detecting application usage with a browser extension is the ability to obtain information on shadow SaaS or unsanctioned and unvetted application use. With access to the internet and a credit card (or not), employees are able to try and use SaaS applications with ease. This discovery option may not be ideal for some organizations, especially those in Europe with privacy rules and workers councils, unless the data captured can be anonymized. Anonymized data does offer some value in terms of providing an understanding of the scope of risk. |
| SSO Platforms | This discovery method works well to detect usage for known or sanctioned applications. SSO data normally captures last login but does not provide usage details at the application feature level. Such information can help you assess premium tier downgrade opportunities. |
| CASB Platforms | With the recent increase in SaaS usage, CASB platform usage is becoming more mainstream. CASBs give organizations the ability to restrict and control access to cloud services from trusted users and devices. CASB tools are great at finding shadow SaaS usage, and blocking or restricting use. CASBs are excellent and identifying and mitigating risk. |
| Financial Systems | Financial systems can provide much information about the SaaS applications you’ve paid for, including a decent inventory of these applications and contract information that is very valuable when preparing for renewals, consolidating contracts, etc. Financial data, however, can be tricky to automatically normalize, and it often requires human review. The lack of usage data and the inability to detect use of free or incorrectly expensed applications also may be possible downsides of this discovery method. |
| Network Traffic | You may be able to capture application traffic within your network by using network monitoring tools. With most employees working from home and many not accessing VPN every day, this method of obtaining visibility to all SaaS application usage is not the best alternative for today’s working-from-home environment. |
| Mobile Device Management | Many SaaS applications are often accessed via mobile devices. Organizations issuing mobile devices and centrally managing them through a mobile device management platform could obtain some visibility into SaaS applications usage on those devices. |
Combining discovery methods
In order to fulfill all use cases outlined above (reduce risk, remove complexity, optimize cost), you may need to employ multiple discovery methods. It is important to note that combining methods increases the accuracy and value of the data collected. Here are some examples you can put into practice:
- Identify applications that are not going through SSO. Capturing usage via browser extensions will inform you of all applications in use. You can then compare this data with applications in use via your SSO platform and determine if there are applications that should be going through SSO.
- Identify users with individual licenses that should be leveraging the corporate agreement. You may have a corporate agreement in one business unit and can detect usage by connecting to the SaaS API, but other business units may be using individual accounts of the same software.
- Assess the value of unused/under-allocated licenses/redundant applications for renewal and rationalization conversations. By marrying application usage data with contract financial details, you’ll have a better understanding of how much these unused premium licenses, unallocated licenses and redundant applications are costing your organization.